Our team works hard to keep your production data safe, secure, and private. It is our responsibility to you, our customers, and we take it seriously. This article answers common questions regarding the security of production data at Evocon.
Who Is the Owner of the Collected Production Data?
The client is the owner of the collected production data from their production site. The only usage of data takes place when the Evocon application is running. Evocon does not use the data itself or share it with third parties. Access to data is provided only to the client and Evocon’s supporting personnel when a support ticket is created.
Where Do We Store Your Production Data?
Evocon is using Amazon AWS as its cloud provider, and from the inception of Evocon, we have been using Amazon AWS European locations for data centers.
What Is the System Architecture of Evocon?
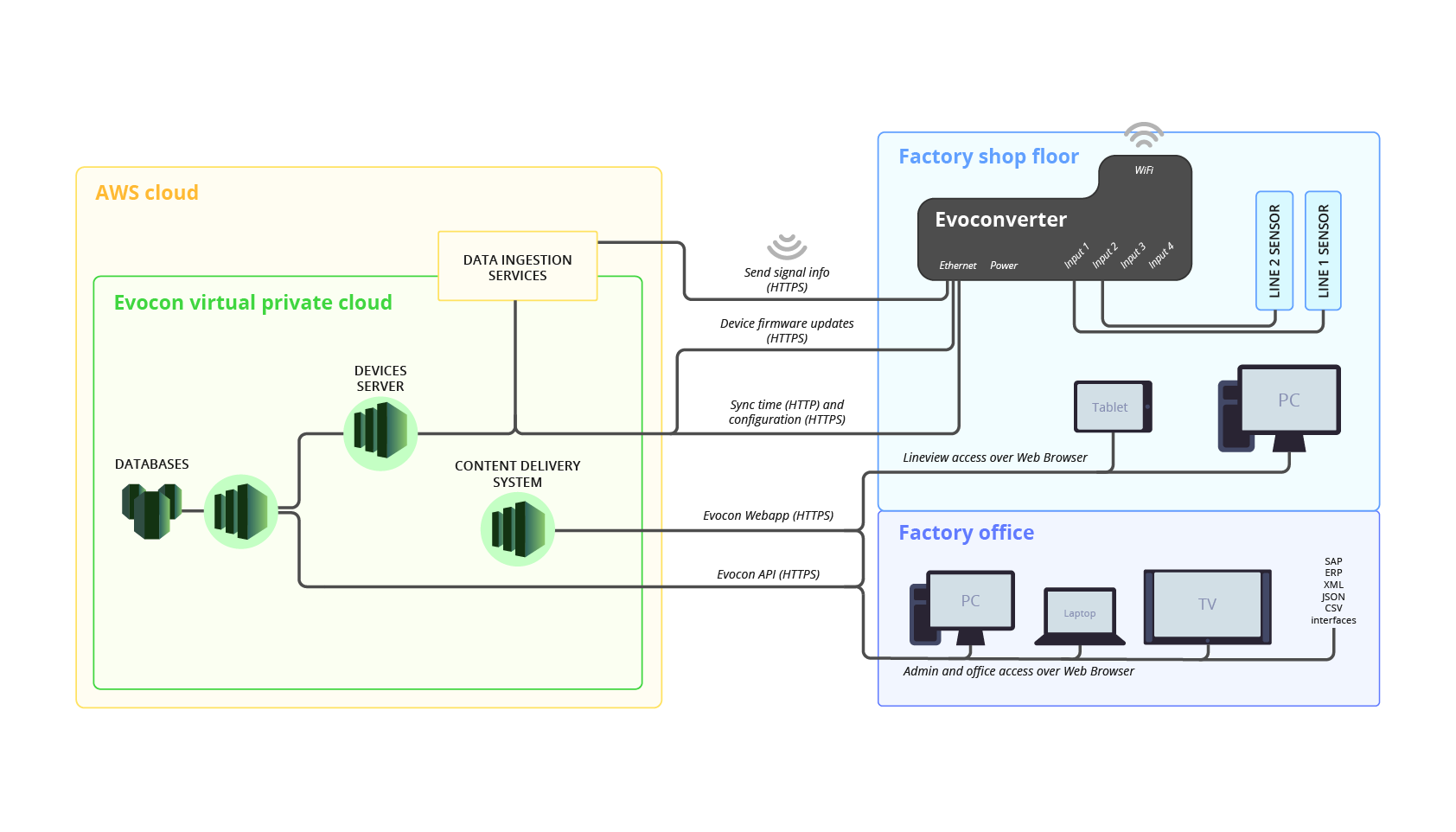
How Do We Secure Your Production Data?
All data transmitted between Evocon and users is encrypted and sent using HTTPS. Furthermore, we encrypt collected and stored production data at rest using an industry-standard AES-256-GCM encryption algorithm. Also, for an Amazon RDS encrypted DB instance, all logs, backups, and snapshots are encrypted.
Connections between internal servers are made in the context of IPSec protected virtual private networks. Server nodes are divided into security groups that restrict access by protocol, IP, and port.
What is AES-256-GCM?
The encryption algorithm for symmetric CMKs is also known as SYMMETRIC_DEFAULT. Currently, this represents a symmetric algorithm based on Advanced Encryption Standard (AES) in Galois Counter Mode (GCM) with 256-bit keys, an industry-standard for secure encryption.
The ciphertext that this algorithm generates supports additional authenticated data (AAD), such as an encryption context, and GCM provides an additional integrity check on the ciphertext. For technical details, see the AWS Key Management Service Cryptographic Details whitepaper.
Data encrypted under AES-256-GCM is protected now and in the future. Cryptographers consider this algorithm to be quantum-resistant. Theoretical future, large-scale quantum computing attacks on ciphertexts created under 256-bit AES-GCM keys reduce the effective security of the key to 128 bits. But, this security level is sufficient to make brute force attacks on AWS KMS ciphertexts infeasible.
DDoS protection
Amazon AWS infrastructure is DDoS-resilient by design. The infrastructure is supported by DDoS mitigation systems that can automatically detect and filter excess traffic.
Learn more: Amazon Web Services
What Is the Data Protection Policy of Evocon?
Data protection model
The model for data storage of tenant data is database-level separation. All tenants have their own separate database where their information is stored. The general data needed for running Evocon services uses a shared model.
Data encryption and protection
We encrypt all sensitive data as stated by law (personal id numbers, social security numbers, etc) to ensure data protection. However, as of 2020 Evocon does not store any information that would categorize as personal.
Employee access to client data
Under normal circumstances, Evocon employees have no access to client data. Two potential situations trigger granting Evocon employees access to client data:
- If Evocon discovers an issue or a malfunction then Evocon contacts the client to ask permission prior to handling the issue.
- If the client sends Evocon a support request, then Evocon considers this also as temporary permission to access client data until we resolve the problem.
Data backup policy
- We back up and replicate tenant databases daily.
- We take snapshots for backups with a 5-minute interval.
- The retention period of backups is 7 days.
- We replicate backup data between different availability zones.
- Only Evocon administrators have access to production servers.
Data handling after contract termination
Evocon administrators delete the databases and backups according to procedures in 7 days upon tenant contract termination.